

To enable us to stay on top of the ever-growing cyber landscape, and mostly because we are all inquisitive about new technology, we regularly research and share new developments in the world of cyber. While definitely not new, in fact dating back to the 5th Century, a current area of further research and learning is data encryption. You may have heard about it recently when the Online Safety Bill sparked interest regarding encryption on platforms such as WhatsApp, Messenger, and Signal.
In an age where data breaches and cyberattacks are rampant, encryption acts as a robust shield, ensuring sensitive information remains inaccessible to unauthorised people. From applications and websites to critical communications links across the world, encryption is used to uphold user privacy, reinforce trust in digital transactions, and to emphasise the importance of data protection in our interconnected world.
Encryption, by making data unreadable without the necessary decryption key, becomes a frontline defence against cyber assaults. So, this Cybersecurity Awareness Month we think it is imperative to champion encryption as a cornerstone of secure, responsible digital practices.
But how does it all work?
Encryption comes in (broadly) two separate flavours: symmetrical and asymmetrical.
With symmetrical key encryption, Bob and Alice share the same encryption key which they both must keep a secret – the encryption key is basically a string of random characters that alter the plain data to make it unreadable for anyone else. It is shared using a key exchange method such as Diffie-Hellman (a mathematical algorithm).
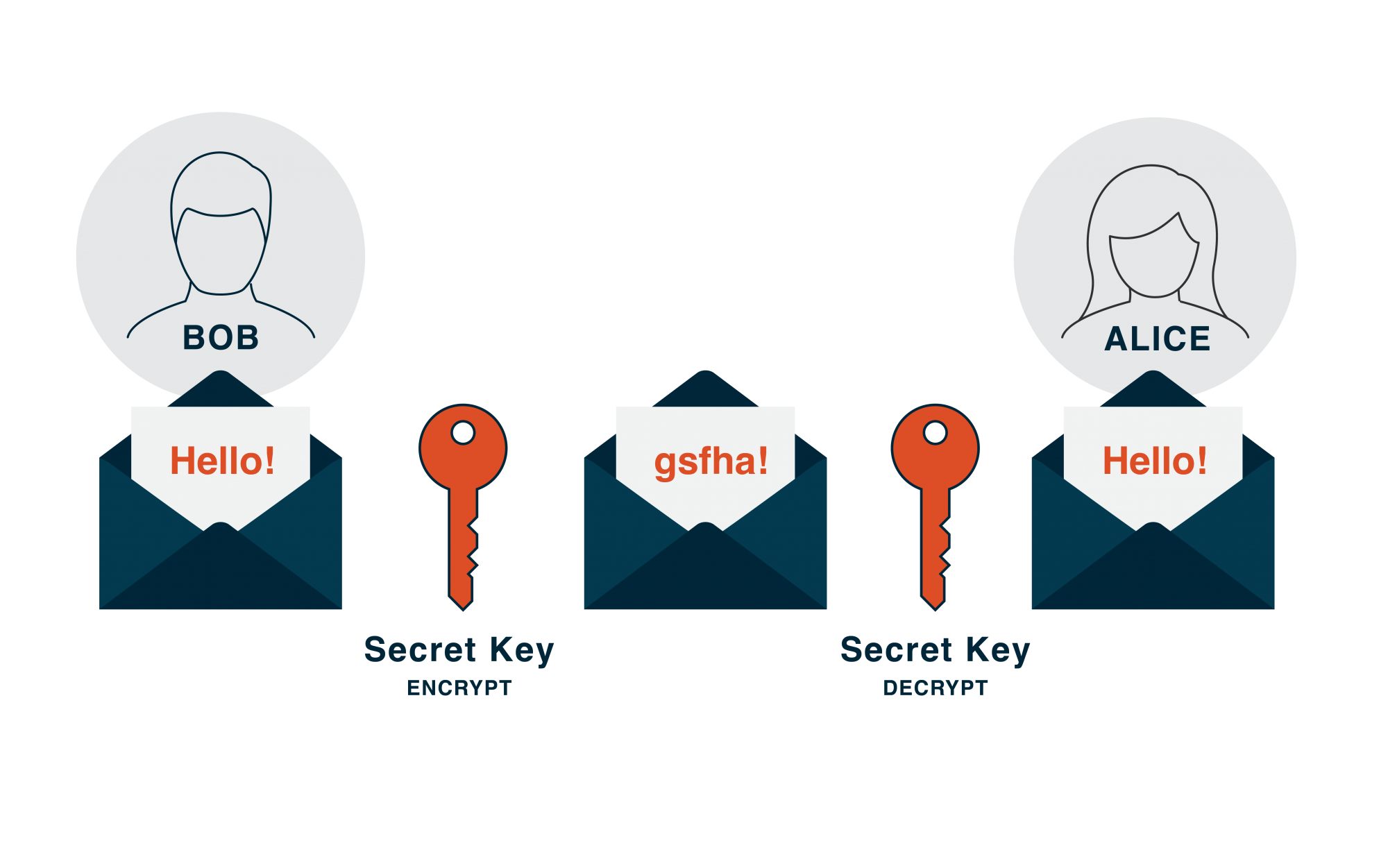 Symmetrical key encryption illustrated
Symmetrical key encryption illustrated
Bob and Alice both use the encryption key to secure the data and send it across the network. As they both have the same key, they can both decrypt the information and read it with the assurance that the data’s confidentiality is intact (assuming the secret key has remained a secret!).
Pros and cons:
✅ Generally faster so better for large amounts of data.
✅ Easier to manage and administrate.
✅ Commonly used for encrypting data storage.
❌ Can be vulnerable when sharing the secret key with the other party.
❌ Not as scalable to big networks (in its purest form).
Asymmetrical key encryption (or public key encryption) is different in the sense that each user has a key pair – one public, shareable with anyone (for example, you could view our website’s public key from within your browser by clicking on the padlock to the left of the address bar), and one private that must be protected.
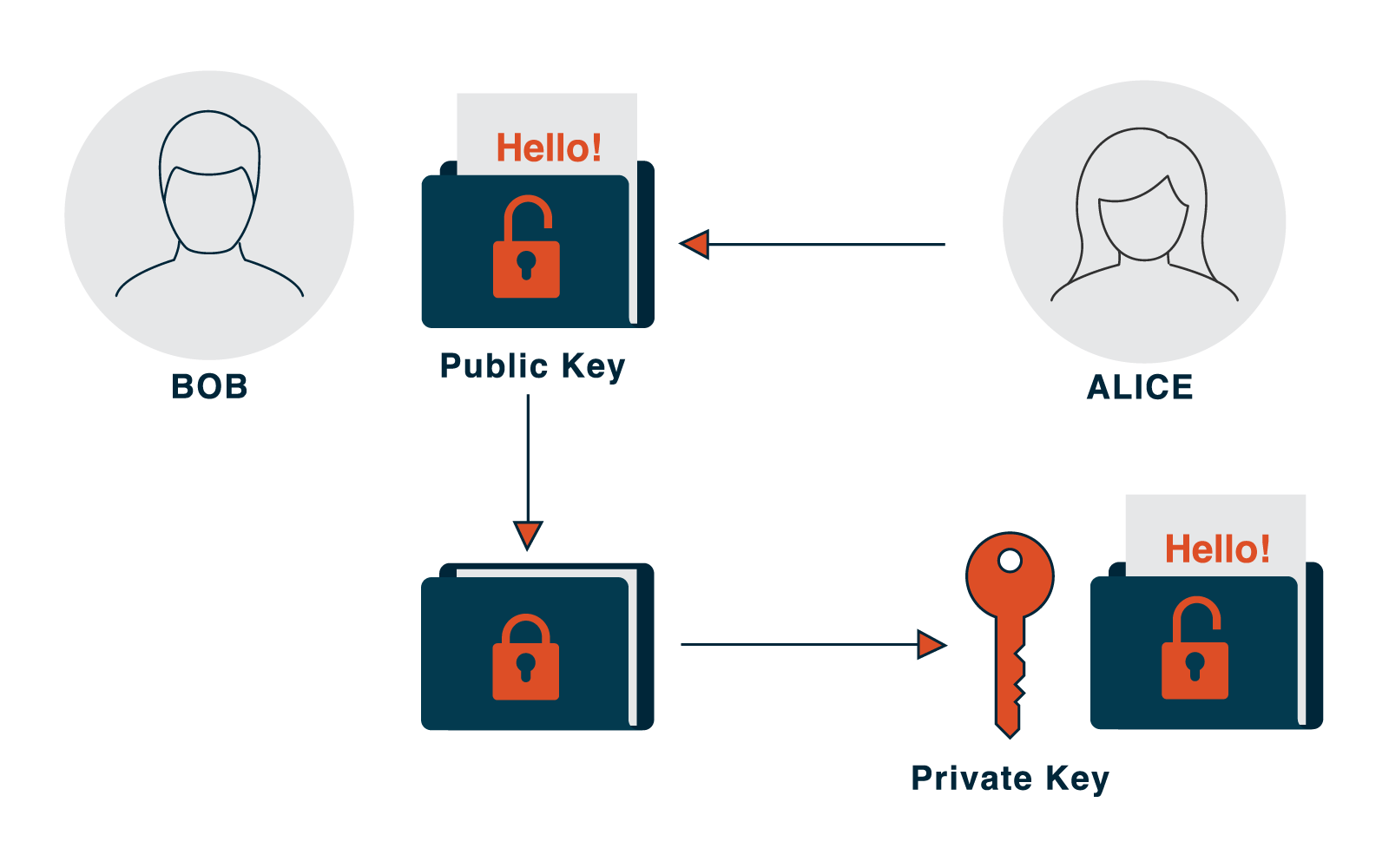 Assymetrical key encryption illustrated
Assymetrical key encryption illustrated
The two keys can be likened to a padlock (public key) and the key for the padlock (private key). If Bob wants to send a secure message to Alice using public key encryption, he will ask her for her padlock. He will then lock the message with this padlock, as he doesn’t need the key to lock it, and send it back to her. Even though everyone on the internet might have seen the padlock, only Alice has the key to open it… and ‘Bob’s your uncle’… public key encryption.
Pros and cons:
✅ Considered more secure as the secret key (or private key) isn’t transmitted publicly.
✅ Can be used for digital signatures to prove identity.
❌ It’s a slower version of encryption and uses more processing power to encrypt and decrypt.
❌ Not as scalable for lightweight devices such as Internet of Thing applications
We are a team of dedicated specialists passionate about assisting organisations in tackling cybersecurity. From hosting cyber ranges and exercises, to securing organisations through cyber vulnerability investigations, and advising on security architecture and cyber risk; we provide a full spectrum of services and take great pleasure in delivering exceptional results for our customers.
If the world of cyber appears intimidating and you are unsure where to begin, please contact us to see if we can assist.
In the meantime, let us use this month to raise awareness and develop a resilient cyber culture!
